- Understanding the Rise of Chinese Open Source Models in Global Technology
- The Intersection of Open Source Innovation and National Security Concerns
- Dissecting the Threat: What Makes Chinese Open Source Models a Security Risk?
- Unpacking the ‘Great Wall of Data’: An Overview of China’s Digital Strategy
- Vulnerabilities in Software Supply Chains: Open Source as the New Front
- The Role of Government in Regulating Open Source Technologies: A Global Perspective
- Analyzing Real-World Cases: Security Breaches Tied to Chinese Open Source
- Technological Sovereignty: How Nations Are Responding to China’s Open Source Surge
- Balancing Innovation with Security: Strategies for Safe Open Source Adoption
- Global Collaboration or Cyber Espionage? The Double-Edged Sword of Open Source Models
- Evaluating the Impact of Chinese Open Source Models on the Global Tech Ecosystem
- Future Trends: Predicting the Evolution of Open Source and National Security
Understanding the Rise of Chinese Open Source Models in Global Technology
A few years ago, if you had asked me about the major players in the open source arena, my answer would probably have leaned heavily on Silicon Valley stalwarts. Fast forward to today, and you’d find me talking a lot about China. The rise of Chinese open source models is not just a trend—it’s a full-blown movement, and it’s reshaping the contours of global technology in ways we’re only beginning to grasp.
China’s foray into open source isn’t incidental or experimental; it’s strategic. The country recognized early on the potential of open source to drive innovation and economic growth. By fostering a robust ecosystem of developers and incentivizing collaboration, China has positioned itself as a formidable force in this space. The Chinese government, tech giants, and an increasingly skilled pool of developers have all converged towards a collective goal: to innovate, scale, and compete on a global level.
What’s fascinating, and perhaps a bit ironic, is the embrace of open source models in a country often associated with stringent information control. Open source is all about transparency and community-driven development, yet China has managed to blend these aspects into its tech fabric while maintaining its unique approach to governance and oversight. The result? An impressive array of open source projects that are not only utilized domestically but are gaining traction internationally.
Chinese tech companies like Alibaba, Tencent, and Huawei are leading the charge, contributing significantly to open source communities. Their projects cover a range of technologies—from artificial intelligence and cloud computing to blockchain and big data. For instance, Alibaba’s open source contributions to big data frameworks have been noteworthy and have caught the attention of international developers looking for robust, scalable solutions.
The appeal of Chinese open source models extends beyond just code. There’s a cultural shift happening as well. Chinese developers are cultivating their own open source ethos, characterized by a spirit of rapid innovation and practical application. This is partly driven by a market that demands speed and efficiency, and partly by the sheer number of tech-savvy individuals eager to make their mark.
However, as we celebrate this open source blossoming, it’s impossible to ignore the accompanying security concerns. The intertwining of global technology networks brings with it potential vulnerabilities. Data privacy, intellectual property theft, and national security risks are at the forefront of discussions as these Chinese open source models become integral to global infrastructures.
While the risks are tangible, it’s worth noting that open source, by its very nature, offers a level of transparency that can help mitigate some security concerns. The collaborative nature of open source means that code is continuously scrutinized by a wide array of developers from around the world, potentially identifying and addressing vulnerabilities more efficiently than proprietary systems.
Navigating this new landscape will require a nuanced approach. Embracing the innovation and economic opportunities that come with Chinese open source models while remaining vigilant about security risks is a delicate balance—one that the global tech community must strive to maintain.
In this unfolding narrative, one thing is clear: China’s open source models are here to stay, and they’re reshaping the global tech ecosystem in profound ways. As we move forward, staying informed and engaged in these developments will be crucial.
![]()
The Intersection of Open Source Innovation and National Security Concerns
When it comes to open source technology, I’ve always marveled at the way it democratizes innovation. There’s something truly empowering about developers from all corners of the globe coming together to create, improve, and share technology without the barriers of proprietary systems. However, the rise of Chinese open source models introduces a new dimension to the conversation—one steeped in both opportunity and caution.
Chinese open source projects have increasingly been making waves, offering robust solutions that compete with Western counterparts. This movement isn’t just about software; it’s about reshaping the global tech landscape. Yet, as with any seismic shift, there are ripple effects that demand our attention—particularly in the realm of national security.
The collaborative nature of open source is a double-edged sword. On one hand, it allows for rapid innovation and refinement, as the collective intelligence of a diverse developer community can swiftly pinpoint and patch vulnerabilities. This aspect of open source software is its greatest strength—the more eyes on the code, the better its integrity. On the other hand, the very openness that facilitates innovation also opens the door to potential exploitation, where malicious actors might embed backdoors or other risks into the codebase.
The global tech community now finds itself at a crossroads. We must embrace the innovation and economic potential that Chinese open source models offer while remaining vigilant about the security implications. This balance isn’t just a path forward—it’s a necessity. As Chinese tech companies continue to gain traction, their influence grows, and with it, the stakes for ensuring that these contributions are both beneficial and secure.
The situation is further complicated by geopolitical tensions. Tech and politics have always been intertwined, but never more so than in today’s digital age. Nations are increasingly aware of the strategic importance of technology, viewing it as both an asset and a threat. Consequently, the scrutiny on any tech product originating from China has intensified, with concerns ranging from data privacy to the strategic use of technology in global power dynamics.
So, how do we navigate this intricate web? It starts with open dialogue and international collaboration on cybersecurity standards. Encouraging transparency and fostering trust are essential steps. Tech companies, governments, and developers must work together to establish protocols that protect the integrity of open source projects, irrespective of their origin.
While these discussions evolve, one thing remains clear: Chinese open source models are here to stay. They’ve carved out a significant niche in the global tech ecosystem, and their influence is undeniable. As we move forward, staying informed and engaged with these developments is not just prudent—it’s imperative.
In this era of digital transformation, the ability to innovate while safeguarding national security isn’t just a challenge; it’s the challenge. I believe that by fostering an environment of collaboration and vigilance, we can harness the full potential of open source technology while mitigating its risks. As always, it’s about finding that delicate balance—one that respects both the power of innovation and the necessity of security.
Dissecting the Threat: What Makes Chinese Open Source Models a Security Risk?
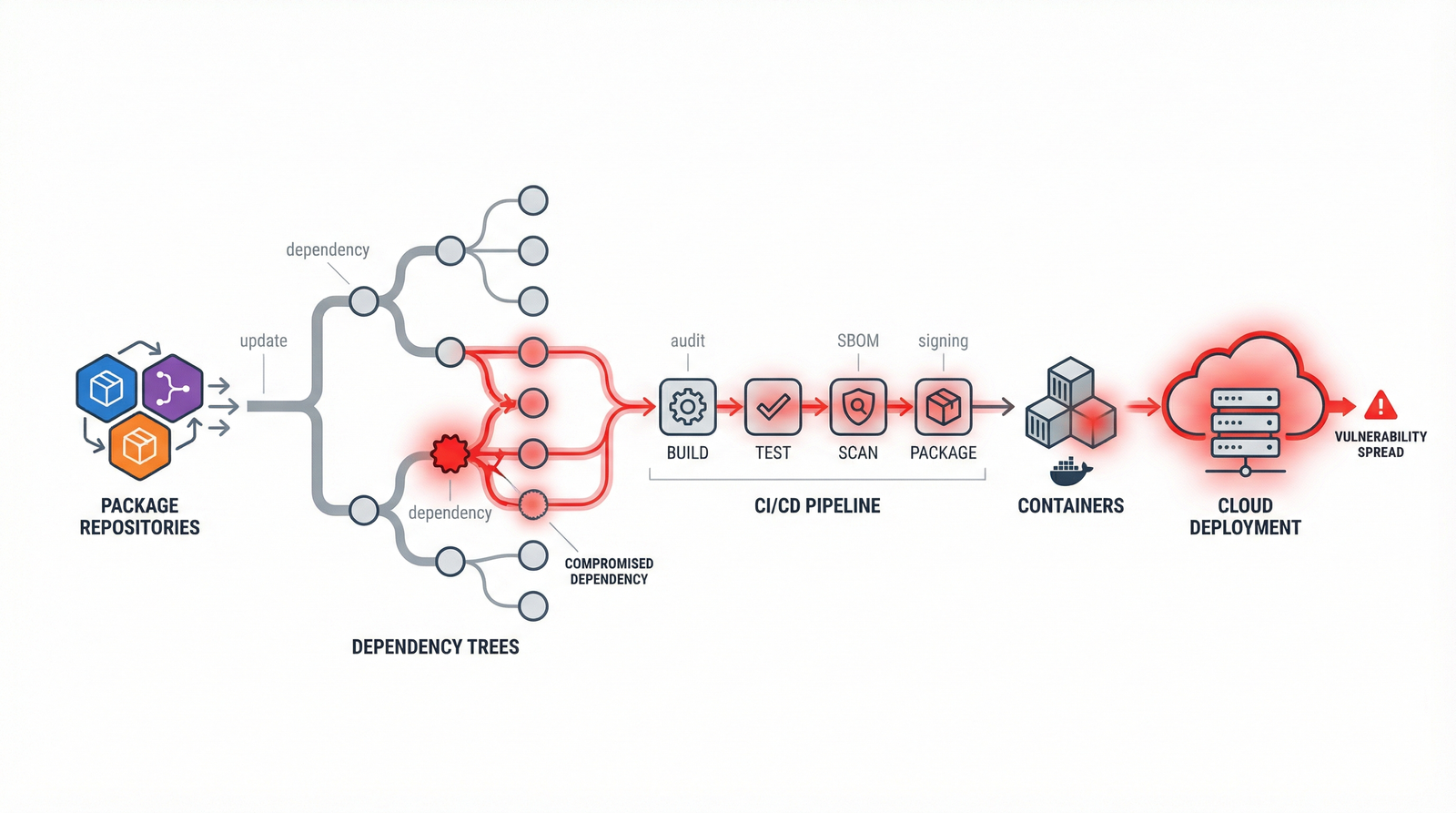
As someone who’s been knee-deep in the tech world for a while, I’ve watched with fascination as Chinese open source models have become a force to be reckoned with. Yet, with their ascendance comes an undercurrent of unease. What is it about these models that raises red flags in the realm of data security?
First off, let’s talk about transparency—or the lack thereof. Open source, by definition, is supposed to be about openness. But when you’re dealing with models developed under the jurisdiction of a state known for its stringent control over information, the waters get murky. The concern is not just about what is visible in the code, but also about what might be lurking in the shadows. Are there hidden backdoors? Could there be undisclosed data scraping functionalities? These are not just rhetorical questions—they’re genuine security concerns that need addressing.
Then there’s the issue of data privacy. Chinese companies are subject to national security laws that require them to cooperate with government requests for data. Even if a Chinese open source project appears innocuous, there’s an unavoidable risk that user data could be requisitioned by the government. In a world where data is the new oil, the implications of such access are profound, affecting not just privacy but potentially national security.
Moreover, intellectual property rights complicate this landscape further. Chinese open source models often draw from a pool of global contributions, which can include patented technology from other countries. The legal tangles here are intricate, creating a labyrinth of potential conflicts over ownership and usage rights. These complications not only pose legal risks but can also stifle innovation by making developers wary of participating.
Of course, it’s not all doom and gloom. The rise of these models is a testament to the vibrant innovation ecosystem in China. Their sheer number and diversity broaden the landscape of technology development, offering new tools and capabilities that can drive progress globally. But with this proliferation comes the responsibility to remain vigilant against potential threats.
It’s also worth noting that this isn’t solely a Chinese issue. Security risks are inherent in open source projects, irrespective of their origin. The key is maintaining a balance between leveraging these powerful tools and protecting the integrity of our data and systems. This is where international collaboration becomes crucial. By working together, tech communities worldwide can establish standards and best practices that mitigate these risks.
In these discussions, staying informed and engaged is vital. As much as we benefit from technological advancements, we must ensure that innovation doesn’t outpace our ability to secure it. The digital transformation is not just changing how we live and work; it’s reshaping the very fabric of international relations and security.
Navigating this landscape isn’t just a challenge; it’s *the* challenge of our time. The goal is to foster an environment where the potential of open source technology can be fully realized without compromising security. It’s about finding that delicate balance, respecting both the power of innovation and the necessity of robust security measures. As we move forward, this balance will be our greatest ally.
Unpacking the ‘Great Wall of Data’: An Overview of China’s Digital Strategy
When I first heard about China’s ambitious digital strategy, it felt like stepping into a futuristic novel where data is the new frontier. What caught my attention was how China is building what many are calling a “Great Wall of Data” — a monumental effort that mirrors the ancient wall’s purpose of fortification but in the digital realm. As we delve into this bold strategy, it’s vital to understand not only its aspirations but also the security risks it presents, particularly as China opens its gates to open source technology.
China’s digital strategy is as multifaceted as it is expansive. It’s not just about increasing internet penetration or boosting technological capabilities. It’s a comprehensive plan to dominate the digital landscape, leveraging open source models that are gaining traction both domestically and globally. By harnessing the power of open source, China is attempting to fuel innovation and collaboration, yet this also introduces a range of security concerns that can’t be ignored.
The allure of open source technology is undeniable. It promises rapid innovation, cost efficiency, and the democratization of technology development. However, as appealing as these benefits are, they come with significant risks, especially when intertwined with China’s broader digital agenda. The transparency that makes open source software so appealing to developers worldwide also poses a potential threat. The same openness that allows anyone to contribute can also allow malicious actors to exploit vulnerabilities.
Navigating this minefield is where the concept of a “Great Wall of Data” becomes particularly pertinent. The wall is symbolic of the protective measures needed to safeguard data integrity and privacy. But it’s more than symbolism; it’s a call to action. We can draw parallels to global standards and best practices that have been established to mitigate these risks. Encryption, access controls, and continuous monitoring are crucial elements in this digital defense strategy.
In these discussions, staying informed and engaged is imperative. As much as we benefit from technological advancements, we must ensure that innovation doesn’t outpace our ability to secure it. The digital transformation is not just changing how we live and work; it’s reshaping the very fabric of international relations and security. We are witnessing a significant shift, and how we respond will define this era.
Navigating this landscape isn’t just a challenge; it’s *the* challenge of our time. The goal is to foster an environment where the potential of open source technology can be fully realized without compromising security. It’s about finding that delicate balance, respecting both the power of innovation and the necessity of robust security measures. As we move forward, this balance will be our greatest ally.
In the end, China’s digital strategy is a double-edged sword. It represents the promise of technological progress, tempered by the imperative of vigilance. As much as we are captivated by the potential of a connected world, we must also be relentless in securing it. Whether the “Great Wall of Data” becomes a bastion of security or a source of vulnerability depends on how we manage these risks. That is the real challenge and opportunity lying before us.
Vulnerabilities in Software Supply Chains: Open Source as the New Front
In this digital age, our software supply chains are under siege, and the new battleground is open-source technology. I’ve been watching the rise of open source models out of China, and I’m both intrigued and concerned. On one hand, they reflect an incredible leap in collaborative innovation. On the other, they present a Pandora’s box of security risks that we can’t ignore.
You see, open-source software’s inherent transparency is its greatest strength—and its greatest weakness. It’s a double-edged sword, much like China’s digital strategy. The open nature of these projects means anyone can inspect the code, contribute to it, or even exploit vulnerabilities if they’re unscrupulous enough. This openness is fantastic for innovation, but it also requires us to be more vigilant than ever.
Take, for example, how supply chains have become increasingly complex. Software isn’t built in a vacuum; it’s assembled from a multitude of components, often sourced from various open-source projects worldwide. Each line of code, each module, is a potential point of entry for malicious actors. And when these components originate from regions with differing cybersecurity norms and regulations, it becomes even more challenging to ensure that everything aligns with the standards we expect.
China’s push into open source has added a new dimension to this dynamic. The country’s strategy is ambitious, aiming to harness the collective expertise of global developers while driving its tech industry forward. It’s an impressive feat, but it also raises questions about governance and security. How do we trust the integrity of software components from a region where state influence can be pervasive?
The risk isn’t just theoretical. We’ve seen incidents where tainted software has slipped through the cracks, and the fallout isn’t pretty. Compromised software can lead to data breaches, espionage, or infrastructure sabotage. It’s not just about hacked emails or stolen credit card numbers. We’re talking about the potential for widespread disruption across sectors that rely heavily on technology.
Our challenge now is to strike a balance. We need the open-source community’s energy and innovation, but we must not compromise security in the process. This means adopting robust vetting processes, improving transparency in software supply chains, and fostering a culture of security-first thinking among developers everywhere.
Collaboration can be our greatest asset, but it must be tempered with caution. This is where policy-makers, tech companies, and developers must come together to create a framework that encourages innovation while safeguarding against risk. It’s about building a “Great Wall of Data” that protects without stifling the very creativity it aims to secure.
As we forge ahead, the delicate dance between embracing open-source potential and implementing ironclad security measures will define our success. If we get it right, we can enjoy the fruits of a connected world without falling prey to its dangers. But if we get it wrong, the consequences could be far-reaching. This is the challenge of our time, and it’s one we cannot afford to ignore.
The Role of Government in Regulating Open Source Technologies: A Global Perspective
Navigating the open-source landscape is a bit like walking a tightrope—you need balance, precision, and nerves of steel. As governments worldwide grapple with the exponential growth of open-source technologies, particularly those emanating from a tech powerhouse like China, striking this balance has never been more crucial. Open-source models offer a treasure trove of innovation, but they come bundled with a Pandora’s box of security risks that cannot be ignored.
Governments have a pivotal role in ensuring that while we harness the potential of open-source, we don’t compromise on security. The challenge is not just about keeping up with technological advancements but also about setting the pace for regulatory frameworks that are both robust and flexible. It’s about creating a “Great Wall of Data” that shields us from threats while allowing the free flow of ideas and innovation.
In many ways, this is a global issue. Open-source technologies are not confined by borders. They thrive on collaboration and shared knowledge, making international cooperation essential. Governments need to engage in dialogues that transcend politics and focus on common goals—protecting citizens and businesses from cyber threats while nurturing an environment where technology can flourish.
Take, for example, the European Union’s General Data Protection Regulation (GDPR). It’s a bold attempt at navigating this complex landscape by enforcing stringent data protection laws. While it mainly addresses privacy, its spirit inspires similar initiatives in the realm of open-source software. The idea is to ensure that developers and companies alike prioritize security from the ground up, embedding it into the DNA of every project.
But regulation is only part of the equation. Governments also have a responsibility to foster innovation. Over-regulation can stifle creativity, driving the brightest minds away from the very platforms we’re trying to secure. Striking the right balance is essential. Policies should be designed to encourage innovation while maintaining rigorous security standards. This could mean providing incentives for companies that invest in secure open-source projects or supporting public-private partnerships that focus on developing secure technologies.
The role of education cannot be overstressed either. Governments should invest in cybersecurity education and awareness programs, ensuring that developers are equipped with the knowledge and skills necessary to build secure software. Encouraging a culture of security-first thinking among developers is critical. It’s not just about creating a safer technological landscape; it’s about instilling trust in the systems we build.
Ultimately, this is a collaborative effort. Governments cannot act in isolation. Tech companies, developers, and policymakers must work together to create frameworks that protect us from threats while fostering innovation. The stakes are high, but the rewards of getting it right—a secure, innovative digital world—are worth the effort.
As we move forward, the interplay between regulation and innovation will shape our digital future. We must build a world where the benefits of open-source models are realized without compromising our security. The challenge is daunting, but with coordinated global efforts, it’s one we can meet with confidence.
Analyzing Real-World Cases: Security Breaches Tied to Chinese Open Source
When we talk about open-source software, especially those stemming from major hubs like China, the conversation inevitably circles back to security. As someone who’s been watching this space closely, I’ve seen both the optimism and the apprehension surround these tools. While the collaborative nature of open-source offers vast potential for innovation, it also opens doors to security vulnerabilities that are sometimes exploited.
Consider the case of a widely-used Chinese open-source library that had an undetected backdoor for months. It was a quintessential example of how something meant to be a boon for developers turned into a bane. The library was integrated into numerous applications, spreading its potential threat far and wide before security researchers caught wind of it. This incident underscored the complexities of ensuring security in open-source software—particularly when the source is thousands of miles away in a nation with different regulatory standards and practices.
Another interesting—and quite alarming—case involved a supply chain attack exploiting a popular Chinese open-source platform. What began as a seemingly benign package update turned into a nightmare as hackers inserted malicious code into the distribution. Developers who trusted the automatic updates suddenly found themselves wrestling with compromised systems. The aftermath of such breaches is not just technical but also trust-related. It erodes faith in the software ecosystems we rely on.
A third case involved deep integration of certain Chinese open-source AI tools into Western systems. These tools, designed for efficiency and performance, inadvertently offered hackers a backdoor. This wasn’t due to any intentional malice on the part of the original developers, but rather the inevitable gaps in security audits and the different threat models considered by different cultures. The breach was a wake-up call about the need for rigorous independent code reviews and the importance of understanding the full scope of software dependencies.
These examples highlight the multifaceted nature of security challenges in open-source software, especially when it crosses international borders. Addressing these issues requires more than just technical fixes; it demands a concerted effort among governments, tech companies, and developers globally.
So, what’s the takeaway for those of us in the tech community? First, we need to foster an environment of transparency and collaboration. It’s crucial that developers everywhere share information about potential vulnerabilities and fixes. Second, we must push for universal standards in security practices that transcend borders. This means advocating for policy frameworks that encourage rigorous testing and validation of open-source software, regardless of origin.
The path forward isn’t without its hurdles. Balancing regulation with the freedom to innovate is a delicate dance. But I’m optimistic. With global cooperation and a shared commitment to protecting our digital world, we can harness the power of open-source while minimizing the risks. The challenges are real, but the opportunity to create a secure and innovative digital future is within our grasp. Let’s approach it with the seriousness it deserves, while keeping an eye on the potential it holds.
Technological Sovereignty: How Nations Are Responding to China’s Open Source Surge
When we talk about open-source software, the conversation often veers into community collaboration, innovation, and the democratization of technology. But as China accelerates its push into open-source models, there’s an undercurrent of concern about data security and technological sovereignty that’s hard to ignore. It’s not just about who builds the technology, but who controls the keys to our digital lives.
For many nations, the surge of Chinese open-source models represents both an opportunity and a challenge. On one hand, China’s contribution to open-source projects can drive innovation and lower costs. On the other, there’s the looming question of security risks and influence. It’s a tightrope walk between embracing technological growth and protecting national interests.
Countries are beginning to wake up to this new reality. There’s a growing movement towards prioritizing technological sovereignty—a concept that’s gaining traction as governments seek to ensure that their digital infrastructure remains secure and within their control. This isn’t about erecting digital walls; rather, it’s about ensuring that technology serves the public interest, without external strings attached.
The European Union, for instance, has been a vocal proponent of digital sovereignty. Their strategy involves investing in domestic tech capabilities and reducing reliance on non-EU technologies. It’s a comprehensive approach that includes everything from bolstering local tech talent to scrutinizing foreign tech acquisitions. The EU’s Digital Markets Act and Digital Services Act aim to provide a robust framework for these efforts, ensuring that tech giants—wherever they originate—play by rules that ensure fair competition and security.
Across the pond, the United States is also grappling with its own set of challenges. American tech giants have long dominated the global landscape, but the rise of Chinese open-source contributions is prompting a reevaluation. While the U.S. remains a hub of innovation, there’s a palpable tension in balancing open collaboration with safeguarding national interests. There’s talk of developing more robust domestic open-source projects and strengthening alliances with like-minded nations to create a unified front against potential threats.
The path forward is undoubtedly complex. The appeal of open-source lies in its transparency and collaborative spirit, but these very traits can be exploited if not carefully managed. Nations need to engage in international cooperation, setting up universal standards that transcend borders. This means advocating for policies that ensure rigorous testing and validation of open-source software, regardless of where it originates.
The challenges are significant, but so too are the opportunities. By approaching this with the seriousness and collaboration it demands, countries can harness the transformative power of open-source technologies while minimizing risks. This is not about stifling innovation but about ensuring that the digital future we build is secure and equitable.
The era of digital fortresses is evolving, and it’s up to all of us—nations, companies, and individuals—to ensure that the Great Wall of Data is one of protection and opportunity, not division. It’s a delicate dance, but with a shared commitment, a secure and innovative digital future is within reach.
Balancing Innovation with Security: Strategies for Safe Open Source Adoption
Navigating the labyrinth of open-source technology, especially in the age of proliferation from countries like China, can be daunting. As someone who has been chronicling the tech world for years, I’ve seen firsthand how the landscape is shifting. Open-source models, with their promise of innovation and efficiency, are reshaping industries. Yet, they also bring with them a slew of security concerns that we cannot afford to ignore.
When we talk about open-source software emanating from China, it’s crucial to understand the dual-faced nature of this beast. On one hand, you have the immense potential for collaboration and advancement. On the other, there’s the looming specter of security risks. The challenge is balancing these two facets—harnessing the power of open-source while safeguarding against vulnerabilities.
One strategy that countries and organizations can adopt is advocating for robust policies that ensure rigorous testing and validation of open-source software. This isn’t about where the software originates but rather ensuring its integrity and security. Comprehensive testing frameworks and validation processes should be standard protocol. By emphasizing transparency and thorough vetting, we can mitigate many of the risks associated with adopting open-source technologies.
Additionally, fostering international collaboration is paramount. Innovation doesn’t happen in a vacuum, and neither does security. By working together, countries can establish best practices and standards that help everyone. This can involve setting up international bodies dedicated to overseeing open-source software testing or even creating collaborative security summits focused on emerging threats and solutions.
Furthermore, investing in cybersecurity education is vital. The more informed and prepared our workforce is, the better equipped we are to tackle potential security threats. This means not just preparing specialists but ensuring that everyone involved in software development understands basic security principles.
Some might argue that these measures might stifle innovation, but I beg to differ. It’s about creating a secure foundation upon which innovation can thrive. By addressing security concerns head-on, we are actually fostering an environment where developers can experiment and innovate without fear of exploitation.
In this digital age, where the Great Wall of Data can either protect or divide us, the path forward lies in unity and vigilance. The opportunities open-source technologies present are vast, but they need to be approached with a seriousness that balances their transformative power with the risks they pose.
Ultimately, this is not a challenge that can be solved overnight. But with a shared commitment to security and innovation, I believe we can build a digital future that is as secure as it is groundbreaking. It’s a delicate dance, but one that’s worth undertaking if we want a world where technology is both a tool for innovation and a bastion of security.
Global Collaboration or Cyber Espionage? The Double-Edged Sword of Open Source Models
In recent years, the open-source movement has surged forward, breaking down barriers and fostering an unprecedented level of collaboration across borders. As someone who’s been following the tech industry for years, it’s fascinating to see how open-source models have enabled developers from every corner of the globe to come together, sparking innovation at a pace that’s often hard to keep up with. Yet, with this surge, we’ve stumbled into a paradox: while these models offer immense potential, they also open up a Pandora’s box of security risks, especially when it comes to Chinese contributions to open-source technology.
With China’s rapid technological advancements, their participation in the open-source community has expanded significantly. On one hand, this global collaboration can be seen as a triumph. It allows for the democratization of technology—anyone, anywhere, can contribute to or benefit from these models. This breaks down the “Great Wall of Data,” making the tech world more interconnected than ever.
However, there’s a flip side. The same openness that drives innovation can also serve as a conduit for cyber espionage. The concern isn’t just theoretical. We’ve seen instances where open-source tools, once benign, have been manipulated for malicious purposes. It’s this double-edged sword that keeps security experts up at night and makes me pause and consider the implications of this brave new world.
To address these concerns, it is essential to establish frameworks that ensure transparency without stifling innovation. I’ve seen firsthand how strict security protocols can sometimes hamper creativity, creating an atmosphere of suspicion rather than collaboration. But ignoring these protocols isn’t an option either. The stakes are too high, especially when we consider the potential fallout of a security breach on a global scale.
The conversation around open-source and security can’t be one-sided. It requires a global effort, a collective commitment to not only understanding the potential threats but actively working to mitigate them. This means engaging with developers, policymakers, and security experts across the world. It’s a tough balancing act—much like walking a tightrope between innovation and caution. But if there’s one thing I’ve learned, it’s that these challenges, while daunting, are not insurmountable.
I believe that with commitment and creativity, we can navigate this landscape effectively. It won’t happen overnight, but with a shared focus on both security and innovation, we can build a digital future that’s not only groundbreaking but secure. It’s about finding that sweet spot where technology serves as a tool for innovation while acting as a bastion of security.
This journey is ongoing. It’s a delicate dance, one where every step matters. But if we manage to keep our eyes on the prize—a world where technology is safe, open, and innovative—we’ll find it’s a dance well worth undertaking. In the end, it’s about ensuring that the ‘Great Wall of Data’ is a barrier against threats, not a divider of potential.
Evaluating the Impact of Chinese Open Source Models on the Global Tech Ecosystem
In the rapidly evolving world of technology, open source models from China have started to play a significant role, and I find myself pondering both their potential and the accompanying security concerns. It’s a fascinating dynamic, this intersection of innovation and apprehension, with Chinese open source models standing tall like a modern-day Great Wall—both a marvel of human achievement and a looming challenge in terms of security risks.
Over the past few years, we’ve seen Chinese tech companies emerging as formidable players in the open source arena. Think of platforms like Alibaba and Huawei, whose contributions to open source projects have started to ripple across the global tech community. However, this rise comes with a juxtaposition of enthusiasm and skepticism, especially from Western countries where security fears dominate discussions around Chinese tech involvement.
The allure of these models is undeniable. They promise innovation at a scale and speed that can be transformative. Yet, as we unlock these capabilities, we also open the door to risks that come with making our systems more reliant on potentially insecure foundations. It’s a bit like discovering an exciting new path in the woods, only to realize it might lead through treacherous terrain. Here, the terrain includes data privacy concerns, intellectual property rights, and the potential for backdoor surveillance—a non-trivial worry in today’s digital landscape.
The impact of these models can’t be understated. On one hand, they democratize technology, leveling the playing field by providing tools that were once the exclusive domain of tech giants. On the other, they challenge existing norms and force us to rethink how we approach security in a world where geopolitical lines blur more each day. We’re not just consumers of technology anymore; we’re participants in a global ecosystem, where the rules of engagement are still being written.
So, how do we navigate this landscape? It requires a delicate balance, a kind of digital diplomacy where we don’t shut the door on innovation but instead open it cautiously. It’s about developing robust international standards and frameworks for data security that accommodate the contributions of all players, including China, without compromising on security.
From my perspective, the key lies in collaboration and vigilance. It’s about fostering an environment where innovation thrives, but not at the expense of our privacy and security. It’s crucial to engage in meaningful dialogues, create transparent policies, and build partnerships that prioritize security while also encouraging technological advancement.
The journey won’t be straightforward, and it certainly won’t be easy. There will be missteps and moments of doubt. But as someone who has watched technology evolve over the years, I’m optimistic. I believe that with commitment and creativity, we can navigate this landscape effectively. It won’t happen overnight, but with a shared focus on both security and innovation, we can build a digital future that’s not only groundbreaking but secure.
Ultimately, it’s about ensuring that the ‘Great Wall of Data’ is a barrier against threats, not a divider of potential. In this dance between innovation and security, every step matters—but it’s a dance worth undertaking.
Future Trends: Predicting the Evolution of Open Source and National Security
In pondering the future of open-source technology and national security, especially through the lens of Chinese contributions, I find myself both fascinated and apprehensive. The rise of Chinese open-source models has sparked a global dialogue around innovation, collaboration, and, significantly, security. As we move forward, these discussions will only deepen, and the decisions we make today will reverberate through the technological landscape for decades to come.
In recent years, China has emerged as a formidable player in the open-source community. This isn’t just about software development; it’s a strategic move, a way for China to assert influence and drive innovation on a global scale. Yet, with this increase in Chinese contribution comes a cascade of security concerns. The open-source nature means that the code is accessible to anyone, and while this openness is the very essence of the community’s strength, it also presents unique challenges in terms of security and trust.
Looking ahead, the evolution of open-source technology in relation to national security will likely hinge on a few key trends. First, there will be an increasing demand for transparency. Governments and organizations will need to establish clear guidelines and standards to ensure that open-source contributions are both secure and reliable. This means rigorous vetting processes and, potentially, the creation of an international regulatory body dedicated to overseeing open-source contributions, especially those with national security implications.
Moreover, I foresee a future where partnerships between nations and tech companies grow more intricate. As issues of trust and security become more pronounced, collaboration will be essential in crafting solutions that balance open innovation with protective measures. These partnerships will need to transcend traditional boundaries, fostering an environment where transparency and security are prioritized without stifling the creative freedom that open-source models thrive on.
Technological advancement should not be stifled by fear, but it must be approached with a strategic mindset. The path will undoubtedly be fraught with challenges—there will be mistakes, and the occasional misstep will be part and parcel of this journey. From my vantage point, having observed technological shifts both monumental and subtle, I’m inclined to believe that our global community can navigate these complexities. It will require a commitment to both security and innovation, treating them not as opposing forces but complementary goals.
The goal is not to build a ‘Great Wall’ that isolates or restricts; rather, it’s to construct a robust defense against potential threats while fostering an environment where innovation can flourish. It’s a delicate balance—a dance between progress and protection. Every step we take matters, and while the path may be long and winding, it’s one that we must pursue with intent and determination.
As we stand on the cusp of this new chapter, it’s clear that the future of open-source technology and national security is a narrative still being written. With thoughtful engagement and a spirit of collaboration, we can shape this story for the better, ensuring that the digital frontier remains both a beacon of innovation and a bastion of security.
Expert Insights & FAQ
The primary security risks include potential backdoors, compromised data privacy, IP theft, and the exploitation of user data through malicious code embedded within the models.
Organizations can conduct thorough code audits, use threat detection tools, collaborate with cybersecurity experts for continuous monitoring, and adhere to software supply chain best practices to mitigate these risks.
Yes, users should consider compliance with laws such as the China Cybersecurity Law, data protection regulations, and be aware of any export restrictions or licensing obligations specific to the software.
Chinese models may have varying security standards and practices compared to Western counterparts. Differences can stem from distinct development protocols, governmental regulations, and focus on specific applications or industries.
The Chinese government supports the development of open source technologies but also implements strict cybersecurity and national security measures, influencing how these technologies are developed and shared.
They introduce complexities in the global cybersecurity landscape by adding diverse security challenges, necessitating international collaboration and standard setting to ensure safe integration and use.